For any engineer or systems administrator responsible for designing a scalable, reliable server infrastructure, the choice of a virtualization platform is fundamental. It defines your operational limit, your deployment speed, and your long-term maintenance costs. When the debate comes down to OpenVZ vs Proxmox, you are comparing two fundamentally different philosophies of server isolation. This is not a simple feature comparison; it’s a choice between the ease of containerization and the deep technical control offered by a hypervisor.
Before evaluating virtualization technology, remember the foundational rule: the host and underlying hardware must be fully trusted, regardless of the hypervisor you choose. If you are strategically initiating virtualization or require a stable foundation, consider partnering with a host that delivers proven infrastructure capability. For instance, reliable web hosting is the mandatory technical prerequisite that allows your chosen virtualization layer to execute without flaw from day one.
Table Of Content
Understanding the Core Difference: Containers vs. Hypervisors
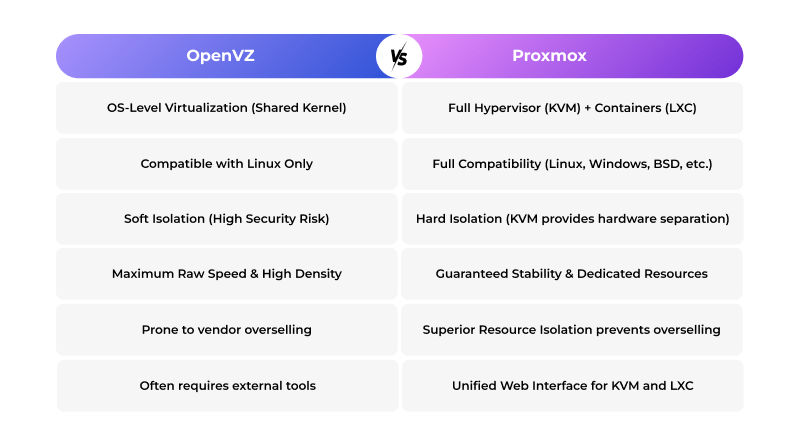
The fundamental distinction between OpenVZ and Proxmox is the method used for core resource isolation. A mistake here immediately destroys performance or creates massive security loopholes at the core.
OpenVZ: Operating System-Level Virtualization
OpenVZ operates as an open-source containerization layer, functioning similarly to the lightweight design of Docker or LXC, but dedicated to complete OS environments. It’s a direct successor of the Linux VServer project. Think of it as sharing a single engine across multiple cars.
How it Works: OpenVZ skips creating a full virtual machine (VM). It just builds isolated containers (sometimes called Virtual Private Servers or VPSs) that all run directly on the host’s Linux kernel. The isolation is at the OS level, not the hardware level.
The Upside of Density: Because there’s no hypervisor or guest kernel to boot up and maintain, these containers are blazing fast, incredibly lightweight, and deliver performance rates that are almost identical to running on bare metal hardware. This is the core efficiency gain, fitting more utility onto every hardware resource available.
The Downside of Uniformity: Every single guest must run the same OS type, like Linux distributions (CentOS, Debian, Ubuntu, etc.). If your stack ever needs to include a Windows Server instance, OpenVZ is not a viable option.
Proxmox VE: The Complete Virtual Environment
Proxmox VE is a comprehensive, Debian-based virtualization management solution. It’s not a single tool; it is a unified platform that expertly combines two distinct virtualization technologies, giving you the best of both worlds under one centralized management interface:
KVM (Kernel-based Virtual Machine): This is the gold standard for full virtualization. KVM creates truly isolated VMs by directly utilizing processor extensions (like Intel VT-x) to simulate physical hardware. This means you can host literally any operating system—Linux, Windows, or specialized BSD environments.
LXC (Linux Containers): Proxmox includes LXC. This works just like OpenVZ, giving you those lightweight containers for Linux jobs that need minimal resource overhead.
Proxmox is the expert’s top recommendation because it offers centralized management for both Kernel-based Virtual Machine and LXC guests. It also includes integrated clustering, advanced software-defined networking, and strong storage management options.
The Technical Calculus: Performance, Isolation, and Flexibility
When a system administrator selects a hypervisor, they are committing to three critical trade-offs that dictate the future stability of the infrastructure.
1. Performance and Overhead: The Density Question
Containers (OpenVZ/LXC) achieve superior speed simply by taking shortcuts. They bypass the need for a separate kernel, giving them an advantage in raw CPU and I/O tasks. For workloads that are extremely I/O-intensive, like running a high-transactional database, OpenVZ often delivers the fastest speeds with zero configuration. This is where many teams first explore a Proxmox vs OpenVZ comparison, especially when balancing density with long-term stability.
However, KVM’s performance, despite having greater resource requirements, is much more reliable because it doesn’t share resources so often. That small loss of speed is often outweighed by the huge improvements in stability and dedicated resources. For instance, complex machine learning tasks using AI powered tools need the dedicated, predictable environment KVM offers, not the potential resource conflicts you get with shared-kernel systems.
2. Isolation and Security: The Kernel Barrier
This is the most crucial dividing line and should be the defining factor for any business requiring compliance or security. When comparing Proxmox LXC vs OpenVZ, the entire discussion relies on kernel isolation and long-term risk management.
OpenVZ/LXC Risk: Sharing a single host kernel among all containers inherently creates a huge security risk. A single, critical vulnerability found in that kernel could potentially be exploited by an attacker to “escape” their container and compromise every single tenant or application on that host. This shared risk demands that you have a rigorous process for applying host kernel patches immediately. This level of risk often complicates mandatory checks for external-facing components and protocols like SSL security.
Proxmox/KVM Security: KVM provides true hardware-level isolation. Each VM possesses its own entirely separate virtual hardware and kernel. If a vulnerability is found in the kernel of a guest OS (say, a Windows VM), the attack is completely isolated within that VM. It cannot bypass the hardware barrier to impact the host or other VMs. This superior isolation is non-negotiable for sandboxing sensitive operations, such as developing a new landing page builder or testing configurations for Azure containers.
3. Operational and Management Reality
The everyday reality of managing your infrastructure—the time spent on maintenance and configuration—will decide the outcome of your virtualization project.
Flexibility is a Core Requirement for IT Growth. Any technical team understands that their requirements won’t stay the same; they’ll evolve over time. For your long-term IT plan to succeed, you must be able to support different kinds of operating systems.
OpenVZ’s Limitation: It is limited to Linux guests only. That’s a big problem if you need to run specialized services that are locked to proprietary operating systems.
Proxmox’s Freedom: KVM is fully compatible with all major operating systems. This high degree of adaptability makes it the definitive choice for any organization anticipating significant growth. This is critical when utilizing specialized tools or needing environments for cross-platform development, such as managing different versions of Figma alternatives. The ability to centrally manage Windows, Linux, and other environments saves a substantial amount of time.
Advanced Storage and Administration
Proxmox is built for large organizations. It features powerful storage solutions like ZFS and Ceph clustering built directly into its web GUI. This provides advanced features like assured data reliability and simplified high-availability without requiring you to manually bolt on complex external solutions. Planning is key for future changes, especially since LXC replaced OpenVZ in Proxmox as the container standard backed directly by the Linux kernel.
Furthermore, consider system recovery. If you are developing and debugging complex code, such as a JavaScript Code Editor, you need reliable, network-independent access. Proxmox provides seamless integration of KVM over IP access for all its guests. This allows administrators to remotely fix boot issues or re-install a damaged OS without the host network even being functional. This level of detailed, non-reliance on the primary network is a massive operational benefit that simplifies disaster recovery and troubleshooting. This feature confirms the platform’s utility as a comprehensive Proxmox virtualization platform.
The Financial Reality: Overselling and Licensing Traps
While OpenVZ and LXC are superior in resource utilization, that density introduces a significant financial risk: the temptation for the vendor to oversell capacity. Because containers share a single kernel, a host can technically oversubscribe its physical resources—CPU cores, RAM, and I/O capacity—to far more guests than the hardware can reliably handle.
This practice, common in budget hosting, guarantees resource contention. Your application’s performance becomes unstable, fluctuating when the host is idle and crashing when another container suddenly demands its full allotted capacity. This scenario defeats the purpose of choosing virtualization for reliability. KVM, by contrast, mandates superior resource isolation. While you lose a bit of density, this setup stops vendors from overselling capacity because every single VM must have its own dedicated, isolated resources to work.
The debate between OpenVZ and Proxmox is less about “which is better” and far more about “which is right for the job at hand.”
OpenVZ (or LXC) is superior in hardware utilization, raw speed, and resource efficiency for environments that are strictly limited to Linux. It’s the lean, fast, economical solution, perfect for non-critical, high-volume needs. It performs its duties efficiently and should be the logical choice when Windows compatibility is not required. However, developers must understand the security trade-offs of using a shared kernel.
Proxmox VE, on the other hand, is a system designed for future growth. It simplifies the difficult technical task of managing a heterogeneous server environment from a centralised interface. For any business building mission-critical infrastructure where security, OS diversity, and scalability are mandatory, Proxmox’s robust, dual-technology approach provides the superior, future-proof path to resilience.
Ultimately, the correct choice is defined by your risk tolerance and future roadmap.
FAQs
1. What container technology did Proxmox replace OpenVZ with?
Proxmox stopped using OpenVZ years ago and switched entirely to LXC (Linux Containers). The reasoning is clear: LXC is the modern standard, built right into the Linux kernel. That’s the whole reason it replaced outdated container solutions, like what was common with OpenVZ in Proxmox’s earlier days.
2. Is OpenVZ still actively maintained and safe to use in production environments?
The truth is, development on that original project has halted. Using unmaintained software for anything important is a huge risk. If a new kernel vulnerability is disclosed, you are fully exposed. You should avoid running OpenVZ in production; the security risk is just too high.
3. How does the security isolation of an OpenVZ container compare to a Proxmox KVM virtual machine?
This is the biggest difference. OpenVZ is soft isolation; all containers share the same kernel, so a major kernel exploit could affect every virtual server on that host. KVM provides hard, hardware-level isolation—it creates a complete virtual PC for each guest. An attack on one KVM instance is contained and cannot breach the host or other VMs.
4. Does OpenVZ support features like live migration and clustering, and how does Proxmox handle these?
Yes, OpenVZ supports basic live migration and clustering, but it is often complex to set up. Proxmox is built to handle this stuff natively. Its platform is designed with features like ZFS and Ceph integration specifically to make clustering and easy, integrated live migration a default operational reality for KVM and Proxmox LXC vs OpenVZ guests.