Choosing the right virtualization technology for your server or VPS setup is crucial. Servers use virtualization to enhance resource efficiency, reduce costs, and enhance flexibility to run multiple VMs (virtual machines). Virtualization increases server hardware utilization and saves power, cooling, and physical space.
So, out of both, if you are struggling to choose the appropriate virtualization technology for your server, here is the right guide. You have too many names around in the digital space. This blog will sort out the best for you.
Table Of Content
What is LXC?
Linux Containers (LXC) is an operating-system-level virtualization method allowing you to operate multiple isolated Linux systems (containers) on a single web host. It uses the Linux kernel’s features, like cgroups and namespaces, to create lightweight, isolated environments. It offers a way to manage processes and resources with less overhead than conventional virtual machines. LXC includes a set of tools, templates, and libraries to create and manage these containers.
When they began the operations in 2001, Linux OS used namespaces. Namespaces helped to isolate different parts of the computer system. The first one was called mount namespaces. It improved the filesystem work and added other namespace types: UTS, IPC, PID, user, and network namespaces. Each namespace helps keep things separate, like hostnames (UTS), inter-process communication (IPC), process IDs (PID), user IDs and permissions (user), and network interfaces (network).
What is OpenVZ?
OpenVZ is a virtualization technology for Linux OS, allowing a single physical server to run multiple isolated Linux containers. VPS hosting server is the best example of virtualization technology. These containers share the host’s Linux kernel. It makes the process lightweight and effective. However, they are limited to operating compatible Linux distributions and cannot be modified at the kernel level.
It was released in 2005 by SWSoft, now known as Parallels. Since then, the OpenVZ team has been working to get their code integrated into the main Linux kernel. This can sometimes be a very slow and painful process. The Xen project went through the same scenario.
OpenVZ vs. LXC: Key Features Comparison
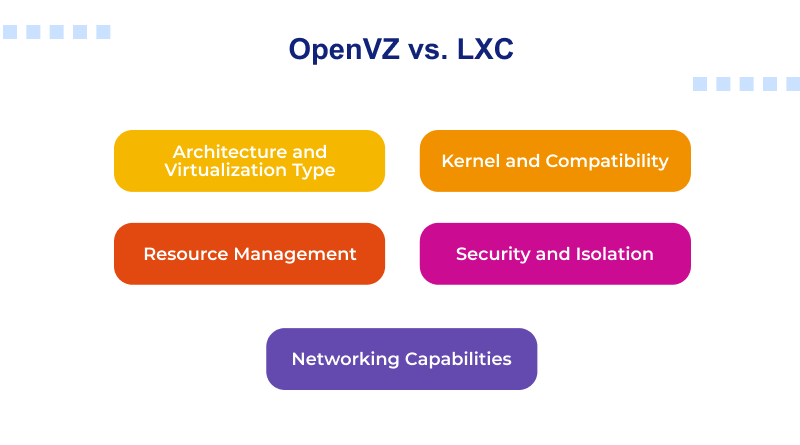
1. Architecture and Virtualization Type
OpenVZ uses a single, modified Linux kernel to operate isolated containers on the same host. Each container acts as an independent server with resources. Hence, OpenVZ utilizes resources effectively, as it doesn’t require hardware emulation or full virtualization layers.
LXC (Linux Containers) uses the standard upstream Linux kernel without patches. It utilizes component features from Linux, like namespaces, cgroups, and seccomp, in order to provide isolation and control. LXC is a lightweight and modular container system that fits natively into the Linux ecosystem, which any developer or sysadmin with an aim in standardizing their containers can embrace.
2. Kernel and Compatibility
OpenVZ requires a modified kernel, which is also a limitation to support new kernel updates and newer distributions. The modified kernel will delay updates and limit users to the kernel version that is supported by the OpenVZ developers. That said, the kernel is still modified for container density and stability to provide enterprise-scale performance in large instances.
Conversely, LXC is developed on the mainline Linux kernel. This means that security fixes are patched sooner and community support is of a higher quality. LXC runs on virtually any modern Linux distribution since it is part of the kernel. As a result, it allows for better integration into DevOps pipelines, automation tools, and CI/CD systems, providing greater ease of adaptability and easier maintenance for the long-haul.
3. Resource Management
OpenVZ offers complete control over server resources using its own parameters like UBC (User Beancounters) and VSwap. These allow administrators to allocate memory, CPU, and I/O limits to each container. It prevents the over usage of resources. However, configuring these settings requires a deeper understanding of OpenVZ’s specific controls.
LXC uses cgroups (control groups) for resource management, which is standard across the Linux ecosystem. Limits on CPU shares, memory, and block I/O are at this level of cgroup programming. This means LXC containers adhere to the same rules and interfaces utilized in other Linux-based services, making it much easier to adjust performance for Linux users who are already familiar with Linux services and tuning.
4. Security and Isolation
OpenVZ containers share a single kernel. It means a kernel-level vulnerability potentially affects all containers. OpenVZ limits container privileges and enhances security. It is a shared-kernel model that poses the higher risks in multi-tenant environments.
LXC has a strong isolation feature by leveraging namespaces to isolate process IDs, file systems, and network interfaces. Additionally, LXC supports unprivileged containers, which greatly limit the potential for escalation from within a container. Finally, when LXC is paired with Linux Security Modules (like AppArmor or SELinux), it provides a strong security measure that is well suited for instances requiring inhibiting security boundaries between applications or users.
Networking Capabilities
OpenVZ employs its virtual networking model. It allows the venet and veth interfaces creation. These features facilitate high-speed communication between host and containers for an ideal-performance-driven setup. However, its custom implementation might not integrate well with modern SDN or container orchestration systems.
LXC can use such standard Linux networking tools as bridging, macvlan, and VLAN tagging, making it very versatile for complex networking topologies. This means that LXC allows administrators to work with advanced network configurations, cloud infrastructures, and Kubernetes clusters without the need for anything else.
5.Use Cases and Ecosystem Support
VPS environments and web hosts use OpenVZ because its performance is predictable. It has outstanding performance for environments where there are plenty of lightweight containers running similar workloads, like shared hosting.
By contrast, for application isolation, testing, and hybrid deployments, LXC remains the preferred method of developers, DevOps teams, and organizations alike. The open standard compatibility that LXC has with other tooling such as Docker, Podman, and LXD allow LXC to be an extension of the broader container ecosystem. Consequently, LXC offers superior scalability and integrations with modern cloud-native applications.
In essence, choosing between OpenVZ and LXC depends on the server objectives and operational flexibility. If maximum efficiency and simplified management with a stable performance for similar workloads are the priorities, OpenVZ is the strong contender. Its optimized kernel and mature ecosystem make it ideal for service providers who value reliability over customization.
Conversely, LXC provides flexibility and present-day integration into the native Linux ecosystem. LXC is better aligned to the needs of developers, system admins, and enterprises attempting to design flexible and scalable environments that match the realities of current containerized infrastructure. With its support for unprivileged containers, use of the mainline kernel, and compatibility with modern orchestration platforms, LXC is the more future-proof choice.
FAQs
1. Which technology is considered a more modern approach to Linux containerization?
The current solutions would be to use Docker preferably, or Podman as an alternative. Docker and Podman use LXC (or the inner components) to provide virtualized environments in containers. They do this by taking advantage of Linux kernel features that help present these environments at an adequate level of abstraction.
2. Does LXC require a custom kernel like OpenVZ, or does it use the mainline Linux kernel?
In comparison, LXC does not require a modified/custom kernel; it uses the standard mainline Linux kernel namespaces and cgroups for isolation features.
3. How does the container isolation mechanism in OpenVZ differ from LXC’s use of namespaces and cgroups?
OpenVZ uses a modified/custom kernel for isolation, and LXC relies on standard, unpatched Linux kernel namespaces and cgroups for isolation.
4. Is OpenVZ still actively maintained, or should users migrate to LXC/LXD?
Since OpenVZ is mostly considered obsolete, and updates to OpenVZ seem to be less frequently developed and used, users are encouraged to migrate to a more recent solution using LXC/LXD (or Docker/Podman).